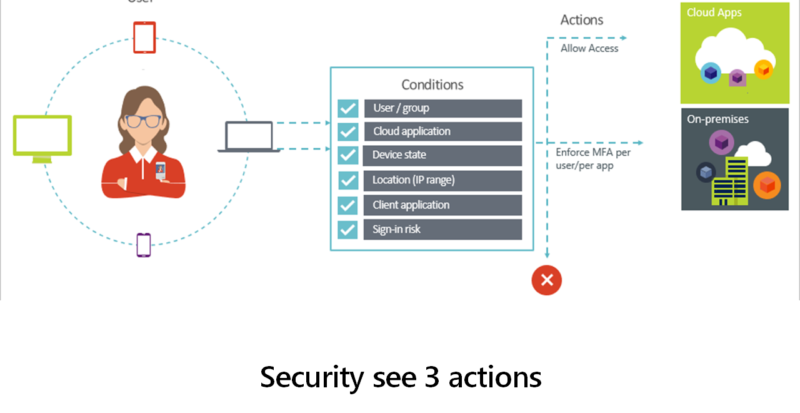
How to disable Entra ID Connect Sync using MSGraph PowerShell
Apart from companies who are “Born in the cloud” and only have cloud identities such as Microsoft Entra ID, most organizations are running hybrid identity and are syncing identity objects such as users, groups and devices from on-premises Active Directory to Entra ID. There are however, more and more companies that wish to migrate to …