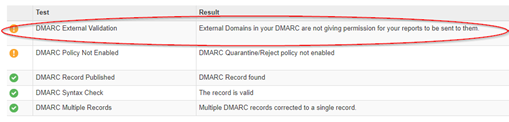
DMARC Alignment
This post is not going to go into the basics of DMARC because there are plenty of resources out there on what DMARC is and how to enforce it. For the purpose of this post, however, I will preface it with saying DMARC is an enhancement on SPF and DKIM email security protocols. I assume …