Down with passwords in Office 365!!
Enabling password-less phone sign-in with the Authenticator App for Office 365 / Azure AD
So, the Password-less phone sign-in with the Microsoft Authenticator app documentation from Microsoft is pretty substantial, but I wanted to add some of my own notes from my experience in enabling phone sign-in on a tenant:
TLDR:
| Admins | Users |
| Enable it in my tenant | Enable it for my user account |
| Revert it for my tenant | Revert it for my account |
One of the requirements documented in the Microsoft Documentation is “End users enabled for Azure Multi-Factor Authentication”. Now we have Azure AD Identity Protection and a policy which enforces MFA Registration but our users are not “enabled” for MFA as you can see in these 2 screenshots:


So I emulated the same in a demo tenant, in fact that is where these screenshots came from. I can confirm that as long as the user has registered for MFA and meets the Authenticator App prerequisites, Phone sign-in works perfectly.
Note:
There is a baseline Conditional Access policy which when enabled will force users with any kind of admin role to MFA on every sign in, I enabled that policy in my demo tenant because the user I was testing with was a global admin, and I thought it needed to present an MFA challenge on every sign in for phone sign-in to work, but even with that policy disabled, phone sign-in works. But having said that, it’s a great idea to enable the baseline policy for your tenant and even remove unnecessary admin roles from users. We use Azure AD Privileged Identity Management (PIM) for that.
The second thing that the documentation doesn’t really elaborate on, is the components of the policy you create in Azure AD using PowerShell. The document simply says run the command:
New-AzureADPolicy -Type AuthenticatorAppSignInPolicy -Definition ‘{“AuthenticatorAppSignInPolicy”:{“Enabled”:true}}’ -isOrganizationDefault $true -DisplayName AuthenticatorAppSignIn
https://docs.microsoft.com/azure/active-directory/authentication/howto-authentication-phone-sign-in
Now if I look at that commandlet, new-azureadpolicy, there’s not much to it, but the thing that caught my attention was the parameter “-isOrganizationDefault”.
NAME
New-AzureADPolicy
SYNOPSIS
Creates a policy.
SYNTAX
New-AzureADPolicy [-AlternativeIdentifier <String>] -Definition <System.Collections.Generic.List`1[System.String]>
-DisplayName <String> [-IsOrganizationDefault <Boolean>] [-KeyCredentials
<System.Collections.Generic.List`1[Microsoft.Open.MSGraph.Model.KeyCredential]>] -Type <String>
[<CommonParameters>]
DESCRIPTION
The New-AzureADPolicy cmdlet creates a policy in Azure Active Directory (AD).
PARAMETERS
-AlternativeIdentifier <String>
Specifies an alternative ID.
Required? false
Position? named
Default value None
Accept pipeline input? False
Accept wildcard characters? false
-Definition <System.Collections.Generic.List`1[System.String]>
Specifies an array of JSON that contains all the rules of the policy, for example: -Definition
@("{"TokenLifetimePolicy":{"Version":1,"MaxInactiveTime":"20:00:00"}}")
Required? true
Position? named
Default value None
Accept pipeline input? False
Accept wildcard characters? false
-DisplayName <String>
String of the policy name
Required? true
Position? named
Default value None
Accept pipeline input? False
Accept wildcard characters? false
-IsOrganizationDefault <Boolean>
True if this policy is the organisational default
Required? false
Position? named
Default value None
Accept pipeline input? False
Accept wildcard characters? false
-KeyCredentials <System.Collections.Generic.List`1[Microsoft.Open.MSGraph.Model.KeyCredential]>
@{Text=}
Required? false
Position? named
Default value None
Accept pipeline input? False
Accept wildcard characters? false
-Type <String>
Specifies the type of policy. For token lifetimes, specify "TokenLifetimePolicy".
Required? true
Position? named
Default value None
Accept pipeline input? False
Accept wildcard characters? false
<CommonParameters>
This cmdlet supports the common parameters: Verbose, Debug,
ErrorAction, ErrorVariable, WarningAction, WarningVariable,
OutBuffer, PipelineVariable, and OutVariable. For more information, see
about_CommonParameters (https:/go.microsoft.com/fwlink/?LinkID=113216).
INPUTS
OUTPUTS
NOTES
------------------ Example 1: Create a policy ------------------
PS C:\>New-AzureADPolicy -Definition <Array of Rules> -DisplayName <Name of Policy> -IsTenantDefault
This command creates a new policy.
RELATED LINKS
Get-AzureADPolicy
Remove-AzureADPolicy
Set-AzureADPolicy
My thoughts were, well what if I wanted to roll this out to certain users in a staged manner, or only users with a certain domain suffix for example. Judging by the documentation on the commandlet help, there doesn’t seem to be a scoping option for the policy other than Org wide.
So it’s either on or it’s off, but each user has to opt into the feature by enabling their account on the Authenticator App anyway so that is staged I guess.
My other concern was how I was going to roll the policy back if I needed to. You’ll be pleased to know, you can simply “remove-azureadPolicy” to roll it back.
Get-AzureADPolicy
Id DisplayName Type IsOrganizationDefault
-- ----------- ---- ---------------------
9e0492ae-3027-4244-a58a-216d3fb9db89 AuthenticatorAppSignIn AuthenticatorAppSignInPolicy True
Remove-AzureADPolicy -Id 9e0492ae-3027-4244-a58a-216d3fb9db89
How to configure password-less (phone) sign-in for Office 365 or Azure AD?
Below explains the steps required either by an Admin of the tenant or individual users to enable password-less sign in.
Configure the tenant (Admin)
Ensure you have the latest version of the Public Preview release of the Azure Active Directory V2 PowerShell Module. You may wish to uninstall and reinstall to confirm this by executing the following commands:
Uninstall-Module -Name AzureADPreview
Install-Module -Name AzureADPreview
Authenticate to the Azure AD tenant to use the Azure AD V2 PowerShell module. The account used must either be a Security Administrator or Global Administrator.
Connect-AzureAD
Create the Authenticator Sign In policy:
New-AzureADPolicy -Type AuthenticatorAppSignInPolicy -Definition '{"AuthenticatorAppSignInPolicy":{"Enabled":true}}' -isOrganizationDefault $true -DisplayName AuthenticatorAppSignIn
Use the authenticator app for phone sign-in (user)
Firstly on your computer go to https://aka.ms/mfasetup
Check the box next to Authenticator app and then click “set up authenticator app” button.
Follow the instructions on the “Configure Mobile app” window (download and install the app on your phone, add an account, scan the barcode etc)
Turn on phone sign-in
Open the Microsoft Authenticator app, go to your work or school account, and turn on phone sign-in:

If you see this icon showing you’re set up.
If this icon appears next to your work or school account name, it means that you’ve already set up phone sign-in for the account. You might be asked to add push notifications for your account, so you can be notified about authentication requests outside of the app.
If you’ve already been using the app and two-factor verification, you can choose the drop-down arrow next to the account name, and then select Enable phone sign-in.
If you can’t find your work or school account on the Accounts screen of the app, it means that you haven’t added it to the app yet. Add your work or school account by following the steps in the Add your work or school account article.
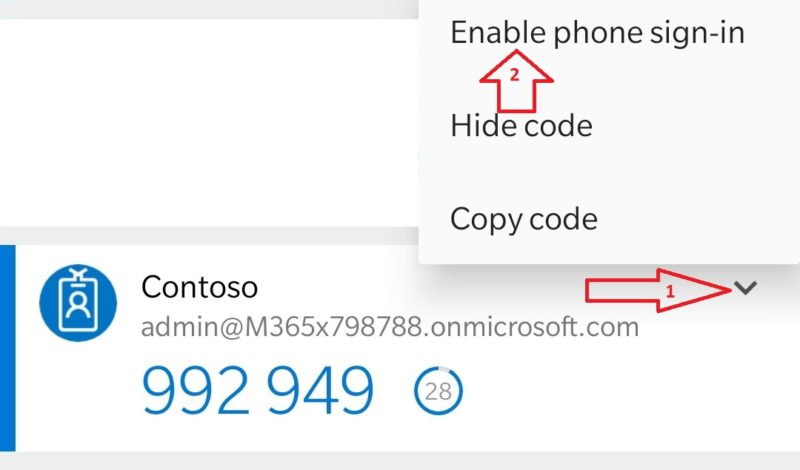
Below are screenshots from the Android Authenticator app:
Click on the drop-down arrow next to the account name (1) and then select Enable phone sign-in (2)

Register the device in AAD (you may have to add your credentials in the app, so make sure you have your password handy) Your tenant needs to allow you to register devices of type (android in this case)


Once the registration is complete, you will go back to the accounts list, and you will notice that the account now has the key icon:

That’s it, you are done setting passwordless sign-in up.
After you turn on phone sign-in, you can sign in using just the Microsoft Authenticator app.
Sign in to your work or school account.
After typing your username, an Approve sign in screen appears showing you a two-digit number and asking you to sign-in through the Microsoft Authenticator app. If you don’t want to use this sign in method, you can select Use your password instead, and sign in using your password.

Open the notification or the Microsoft Authenticator app on your device, and then tap the number that matches the number you see on your computer’s Approve sign-in screen.

Choose Approve if you recognize the sign-in attempt. Otherwise, choose Deny.
Use your phone’s PIN or your biometric key to complete the authentication.
Reverting back to using a password (User)
Should you prefer typing in a password each time (yuk!) then you can revert to password sign on by unregistering your phone. You will still be able to use the Authenticator App for MFA codes when required to do so.
In the settings area of the Authenticator app (…), select Device Registration under Work or school accounts

Then, click unregister. The phone will be unregistered from AAD and the phone sign in will be disabled for your user account only.

Revert passwordless sign-in for the tenant (Admins)
To revert this functionality for the entire tenant, simply remove the Azure AD policy that was created when you enabled it.
Get-AzureADPolicy
Id DisplayName Type IsOrganizationDefault
-- ----------- ---- ---------------------
9e0492ae-3027-4244-a58a-216d3fb9db89 AuthenticatorAppSignIn AuthenticatorAppSignInPolicy True
Remove-AzureADPolicy -Id 9e0492ae-3027-4244-a58a-216d3fb9db89