DMARC and External domain verification
This post is not going to go into the basics of DMARC because there are plenty of resources out there on what DMARC is and how to enforce it. For the purpose of this post, however, I will preface it with saying DMARC is an enhancement on SPF and DKIM email security protocols. I assume you have an understanding of DNS TXT records, and how to check them using nslookup for example.
DMARC external domains verification
In your DMARC DNS record, you may be sending aggregate and or forensic reports to a reporting service such as Valimail or Dmarcian etc. You may also be sending them to another recipient on one of your other company domains. To do so you would need to specify a mailto: recipient with a domain other than the domain for which you are configuring. For example the DMARC record for apples.com might look like this:
"v=DMARC1; p=none; rua=mailto:dmarc_agg@vali.email,mailto:reports@bananas.com"According to RFC-7489 section 7.1, It is possible to specify destinations for the different reports (rua and ruf) that are outside the authority of the Domain Owner making the request.
This allows domains that do not operate mail servers to request reports and have them go someplace that is able to receive and process them (reports@bananas.com).
Without checks, this would allow a bad actor to publish a DMARC policy record that requests that reports be sent to a victim address, and then send a large volume of mail that will fail both DKIM and SPF checks to a wide variety of destinations; the victim will in turn be flooded with unwanted reports. Therefore, a verification mechanism is included.
MXToolbox checks this for you if you are checking the DMARC record and will tell you if this external verification mechanism is failing
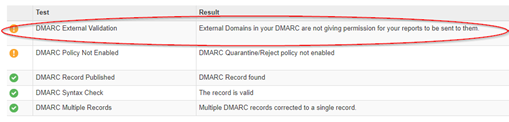
In my Apples.com example above, the bananas.com domain needs to have a TXT DNS record for
"apples.com._report._dmarc.bananas.com" "v=DMARC1"Alternatively, if bananas.com is going to receive reports for a large number of domains, or any domain, bananas.com can have a wildcard TXT DNS record of:
"*._report._dmarc.bananas.com" "v=DMARC1"This would confirm that bananas.com is willing to receive DMARC reports for any
domain.
Valimail and other DMARC report services have the latter configured and that is why you can send reports to them without any issues. This is confirmed in the DNS record for vali.email
nslookup -q=TXT *._report._dmarc.vali.email
Non-authoritative answer:
*._report._dmarc.vali.email text =
"v=DMARC1;"So, if you are going to specify reports to be delivered to another domain, and it is not a DMARC reporting service like Valimail or Dmarcian, then you need to have either a specific validation record or a wildcard validation record.
My experience is that people don’t know what to do with the aggregate and forensic reports if they receive them, so it’s better to let a reporting service deal with them and simply remove the custom recipient address from your DMARC DNS record.
Using Valimail Enforce?
Valimail, and I’m sure others have an option to add External Reporting Domains in the Domains section of your domain:
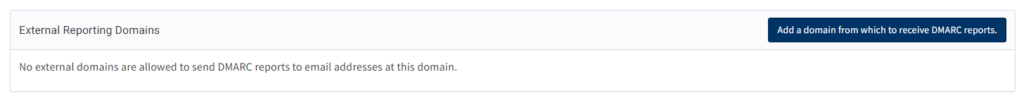
According to Valimail, it is not necessary to specify “External Reporting Domains” for external domain validation when using Valimail Monitor. The external domain verification feature is primarily used in the Valimail Enforce product if you were wondering what that feature was for.
