How to Deploy Zero Trust in minutes
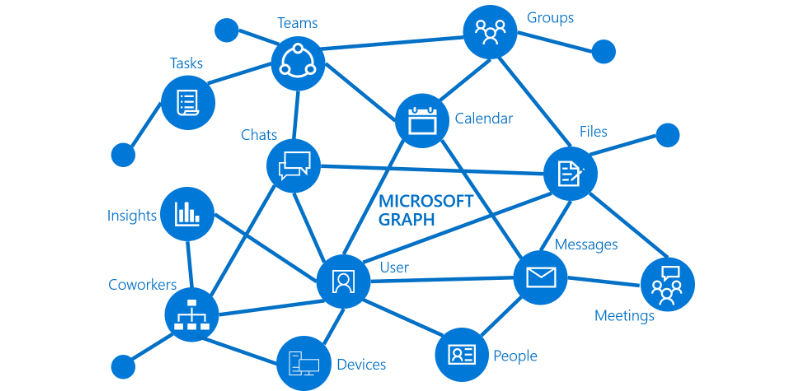
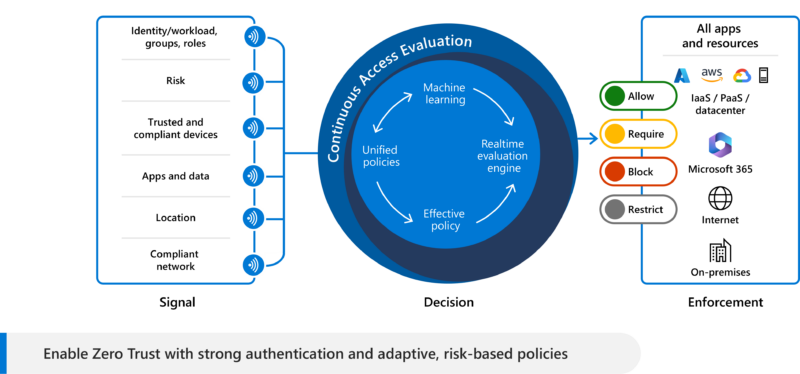
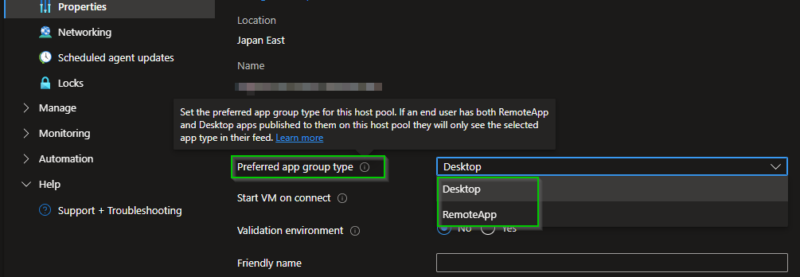
Deploy 14 Entra ID Conditional Access Policies in minutes to enable your Zero Trust security strategy Microsoft 365 and Office 365 advanced deployment guides help you set up and deploy your tenant, apps, and services. They include best practices, security features, collaboration tools, and scripts for faster deployment. You can access these guides in the …